Satu-satunya soal steganografi di final Gemastik XII, poin 200.
Intro
File yang diberikan berupa
$ file minatozaki.bmp
minatozaki.bmp: bzip2 compressed data, block size = 600k
TLDR
- Extract
- Extract
- Brute force password to extract
- Extract
- Baca Spectogram
- Get the flag
Full Steps
Meskipun file berekstensi bmp, ketika dicek dengan file menandakan bahwa file tersebut adalah bzip compressed data sehingga dilakukan ekstraksi data
$ 7z e minatozaki.bmp
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,4 CPUs Intel(R) Core(TM) i5-6200U CPU @ 2.30GHz (406E3),ASM,AES-NI)
Scanning the drive for archives:
1 file, 6737180 bytes (6580 KiB)
Extracting archive: minatozaki.bmp
--
Path = minatozaki.bmp
Type = bzip2
Everything is Ok
Size: 9652224
Compressed: 6737180
Didapatkan file minatozaki
$ file minatozaki
minatozaki: POSIX tar archive
Extract lagi
$ tar -xvf minatozaki
cheese_kimbap.wav
$ file cheese_kimbap.wav
cheese_kimbap.wav: RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, stereo 44100 Hz
Merupakan audio potongan dari sebuah acara TV dan ketika dibuka dengan Audacity, tidak ada pola-pola yang mengarah pada analisis Spectogram maupun SSTV, sehingga kemungkinannya antara Steghide atau LSB.
$ steghide extract -sf cheese_kimbap.wav
Enter passphrase:
steghide: could not extract any data with that passphrase!
Steghide dengan password kosong tidak dapat mengekstrak data apapun, kemungkinan password harus ditebak. Gunakan tool StegCracker [1] dan wordlist 00-indonesian-wordlist.lst [2] untuk mencari password-nya
$ stegcracker cheese_kimbap.wav ~/ctf/tools/wordlist/indonesian-wordlist/00-indonesian-wordlist.lst
StegCracker 2.0.7 - (https://github.com/Paradoxis/StegCracker)
Copyright (c) 2019 - Luke Paris (Paradoxis)
Counting lines in wordlist..
Attacking file 'cheese_kimbap.wav' with wordlist '/root/ctf/tools/wordlist/indonesian-wordlist/00-indonesian-wordlist.lst'..
6/79898 (0.72%) Attempted: afkirorns
Didapatkan password-nya adalah
patriot
File berikutnya memiliki ekstensi .zip, extract lagi
$ file cheese_kimbap.wav.out
cheese_kimbap.wav.out: Zip archive data, at least v?[0x314] to extract
$ mv cheese_kimbap.wav.out cheese_kimbap.wav.zip
$ unzip cheese_kimbap.wav.zip
Archive: cheese_kimbap.wav.zip
inflating: further.wav
Buka dengan Audacity
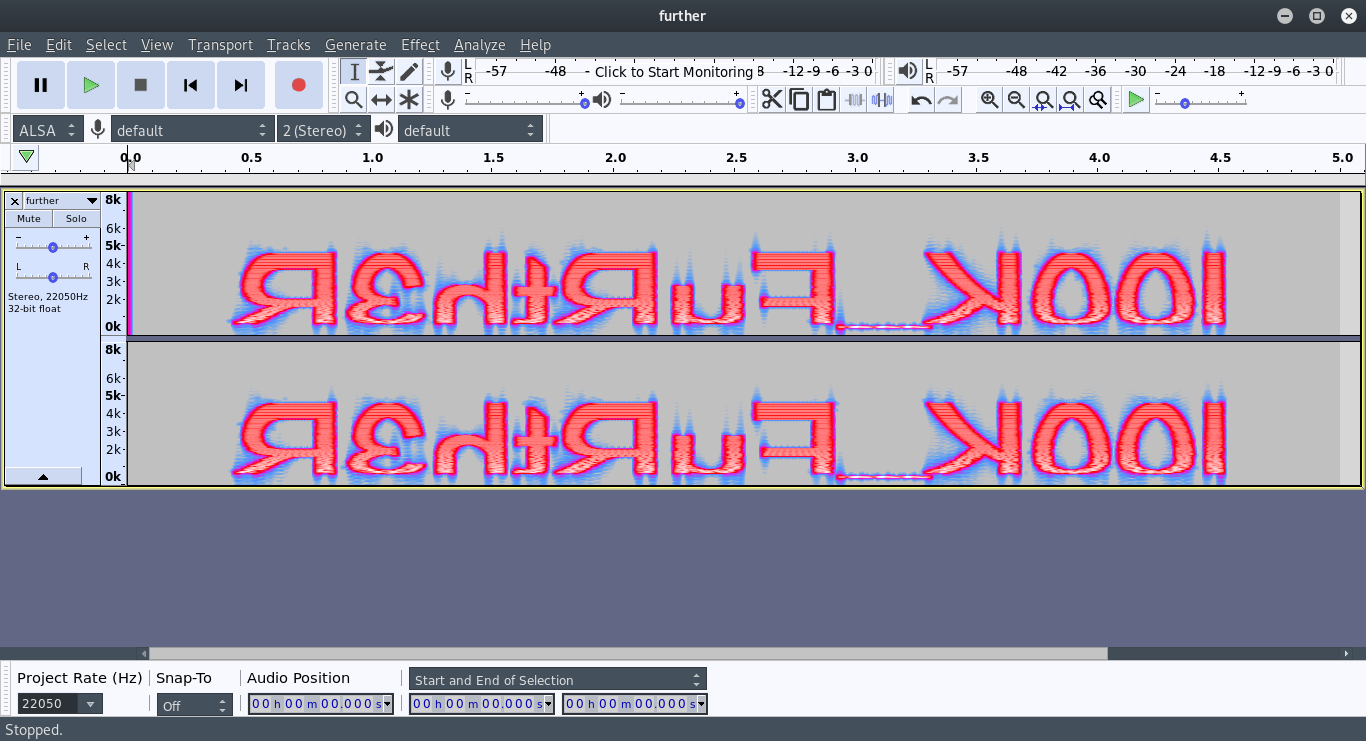
Flag
gemastik12{looK_FuRth3R}
References
Rant
Selesaikan apa yang sedang dijalankan, jangan baru 40% langsung di-CTRL+C dudul