Soal Forensik pertama yang diberikan saat final Hology 2.0, starting points: 100.
Intro
File yang diberikan berupa
$ file Leaked
Leaked: data
TLDR
- Perbaiki file
- Import registry
- Analisis registry
- Extract hex value
- Decode
- Get the flag
Full Steps
Isi dari file Leaked adalah
$ cat Leaked
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa��Windows Registry Editor Version 5.00
(...)
[HKEY_CURRENT_USER\Software\Microsoft\XboxLive]
(...)
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAaa
Yang pertama dilakukan adalah menghapus string sampah aaaaaa… di awal file dan AAAAA… di akhir file
f = open('Leaked','r').read()
g = f[205:-243]
h = open('Leaked.reg','wb')
h.write(g)
h.close()
Setelah dipotong, file Leaked.reg menjadi
$ file Leaked.reg
Leaked.reg: Windows Registry little-endian text (Win2K or above)
Baru kemudian dibaca kembali isi dari file Leaked.reg, dan didapatkan baris yang menarik
"C:\\Users\\hanyi\\source\\repos\\Flag\\Flag\\obj\\Debug\\Flag.exe"=hex:53,41,\
43,50,01,00,00,00,00,00,00,00,07,00,00,00,28,00,00,00,00,68,0a,00,00,00,00,\
00,01,00,00,00,00,00,00,00,00,00,00,0a,65,22,00,00,bf,a2,13,9d,ed,d1,d3,01,\
00,00,00,00,00,00,00,00,02,00,00,00,28,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,9d,0d,00,00,00,00,00,00,01,00,\
00,00,01,00,00,00
"C:\\Users\\hanyi\\Desktop\\Flag.exe"=hex:53,41,43,50,01,00,00,00,00,00,00,00,\
07,00,00,00,28,00,00,00,00,68,0a,00,00,00,00,00,01,00,00,00,00,00,00,00,00,\
00,00,0a,65,22,00,00,bf,a2,13,9d,ed,d1,d3,01,00,00,00,00,00,00,00,00,02,00,\
00,00,28,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,2c,4c,00,00,00,00,00,00,01,00,00,00,01,00,00,00
Langkah selanjutnya adalah melakukan Import Leaked.reg menggunakan regedit. Hal yang aman adalah dengan menggunakan Virtual Machine, namun ketika pelaksanaan kemarin karena tidak memiliki VM yang ready, saya yolo saja dengan mengimport-nya ke regedit di Wine (setidaknya kalau broken, yang broken hanya Wine saja).
$ wine regedit
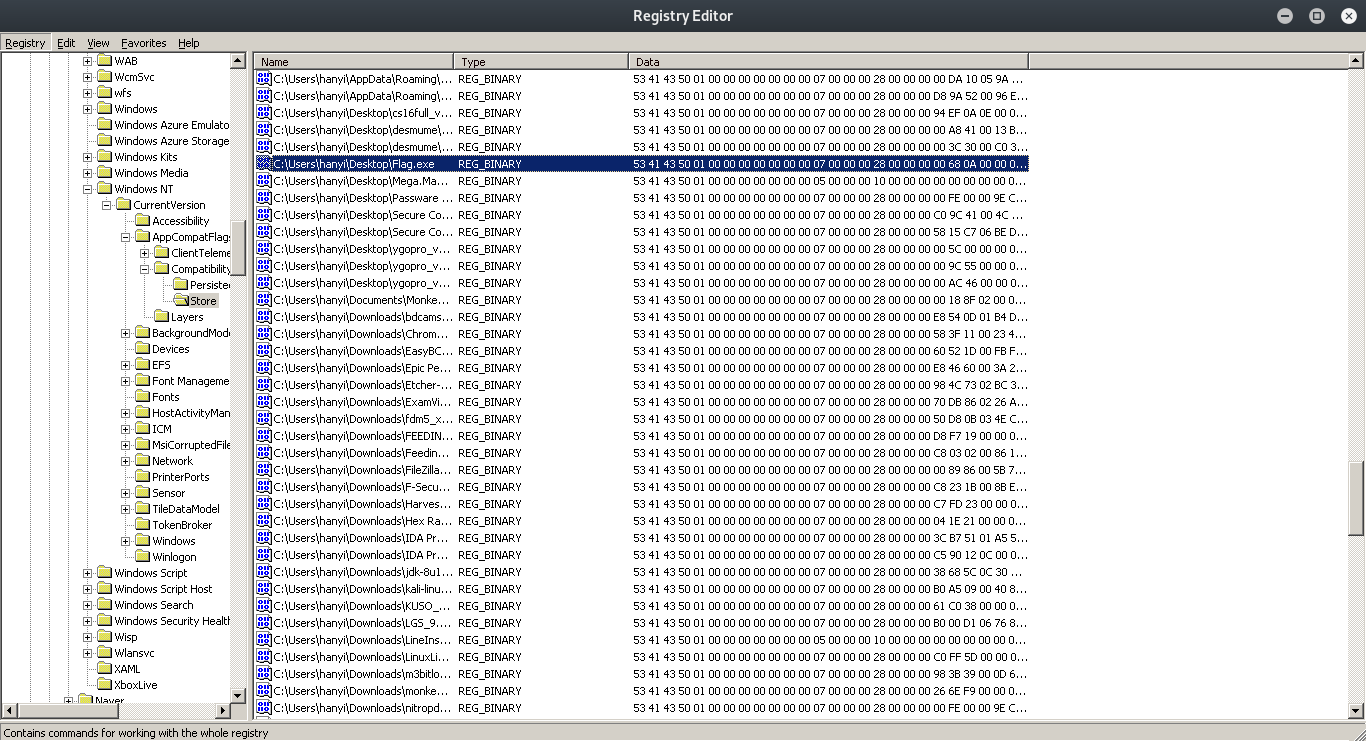
Ditemukan Flag.exe di [HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store]
Hint yang diberikan panitia adalah:
- Display Opened Application in Jendela
- ROT-13
Berdasarkan hint, dilakukan pencarian dengan keyword:
windows registry rot 13
dari referensi [1] diketahui bahwa system objects seperti program, shortcut, dan control panel applets yang baru saja diakses akan disimpan di
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist
dalam bentuk ROT-13 Encoded
Setelah dicari dengan regedit, ditemukan IHYA_INYHRF yang jika dilakukan ROT-13 menjadi VULN_VALUES, kami mengasumsikan bahwa ini merupakan hasil run dari file flag.exe tadi.
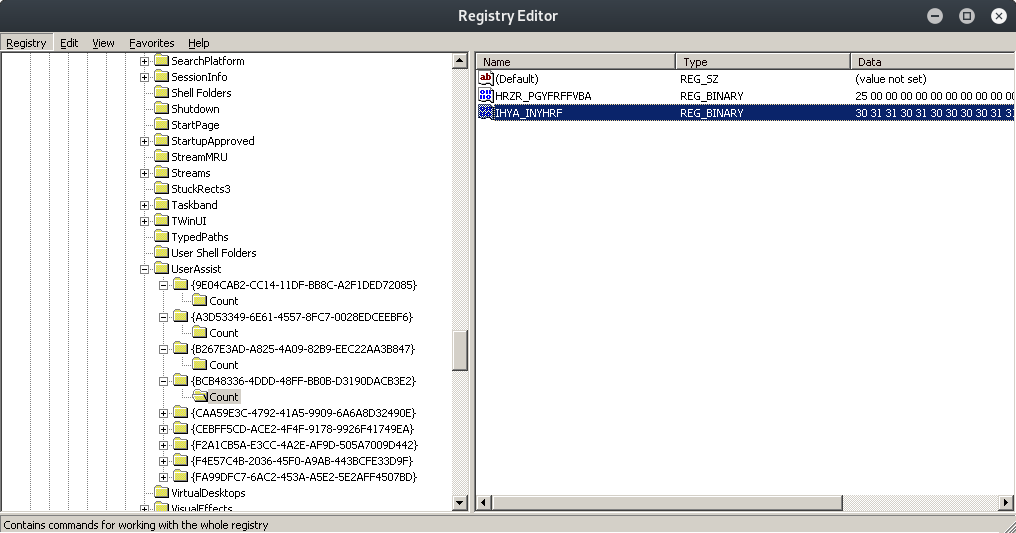
Ambil data-nya, kemudian buat script-nya
solver.py
from Crypto.Util.number import long_to_bytes
ihya="30,31,31,30,31,30,30,30,30,31,31,30,30,30,31,31,30,31,31,31,30,31,30,30,30,31,31,30,30,31,31,30,30,31,31,31,31,30,31,31,30,31,31,31,30,30,31,30,30,30,31,31,30,30,30,30,30,31,31,31,30,31,30,30,30,31,30,31,31,31,31,31,30,30,31,31,30,30,30,31,30,30,31,31,30,30,31,31,30,31,30,31,31,31,31,31,30,31,31,30,30,31,30,30,30,31,31,30,30,31,30,31,30,31,31,30,30,31,31,30,30,31,31,30,30,30,30,31,30,31,30,31,30,31,30,31,30,31,31,30,31,31,30,30,30,30,31,31,30,31,31,31,30,31,30,31,31,31,31,31,30,31,31,31,30,30,31,30,30,30,31,31,30,30,31,31,30,31,31,30,30,31,31,31,30,30,31,31,30,30,30,31,30,31,31,31,30,30,31,31,30,31,31,31,30,31,30,30,30,31,31,31,30,30,31,30,30,31,31,31,31,30,30,31,30,31,30,31,31,31,31,31,30,31,31,30,31,31,30,31,30,31,31,30,30,30,30,31,30,31,31,30,31,30,31,31,30,30,31,31,30,30,31,31,30,30,31,31,30,31,30,31,30,31,30,31,31,31,31,31,30,30,31,31,30,30,31,31,30,31,31,30,30,30,30,31,30,30,31,31,30,31,30,31,30,31,31,31,31,30,30,31,30,31,31,31,31,31,30,31".split(',')
flag=''
for i in ihya:
flag+=i.decode('hex')
print(long_to_bytes(int(flag,2)))
Flag
hctf{r0t_13_defaUl7_r3g1stry_mak35_3a5y}
References
Rant
Baru dapet step 4 waktu tinggal 30 detik, alhasil gagal solve on time alias woe tambahin 5 menit lagi aja solve ini saya …