Stegano 2 Indoxploit
Intro
File yang diberikan berupa
$ file who-is-this.zip
who-is-this.zip: Zip archive data, at least v?[0x314] to extract
$ unzip who-is-this.zip
Archive: who-is-this.zip
creating: who-is-this/
inflating: who-is-this/lol.jpg
inflating: who-is-this/readme-first
TLDR
- Steghide
- Susun script solver-nya
- Get the flag
Full Steps
Baca pesan di readme-first terlebih dahulu
# can u read this bruh ??
aGVsbC1vIG04LCBpIGFtICJoaWRpbmciIGluc2lkZSB0aGUgcGljdHogLi4=
aWYgdSB3YW50IHRvIGxvb2sgYXQgbWUsIHBseiB1c2UgYSB0ZXh0IGluc2lkZSBhICJyZWQgbGluZSIgYXMgYSBrZXkgLi4=
R0xIRiAhISBpdCBjb3VsZCBiZSBFWiA0IFUgLi4=
Decode Base-64, menjadi
hell-o m8, i am "hiding" inside the pictz ..
if u want to look at me, plz use a text inside a "red line" as a key ..
GLHF !! it could be EZ 4 U ..
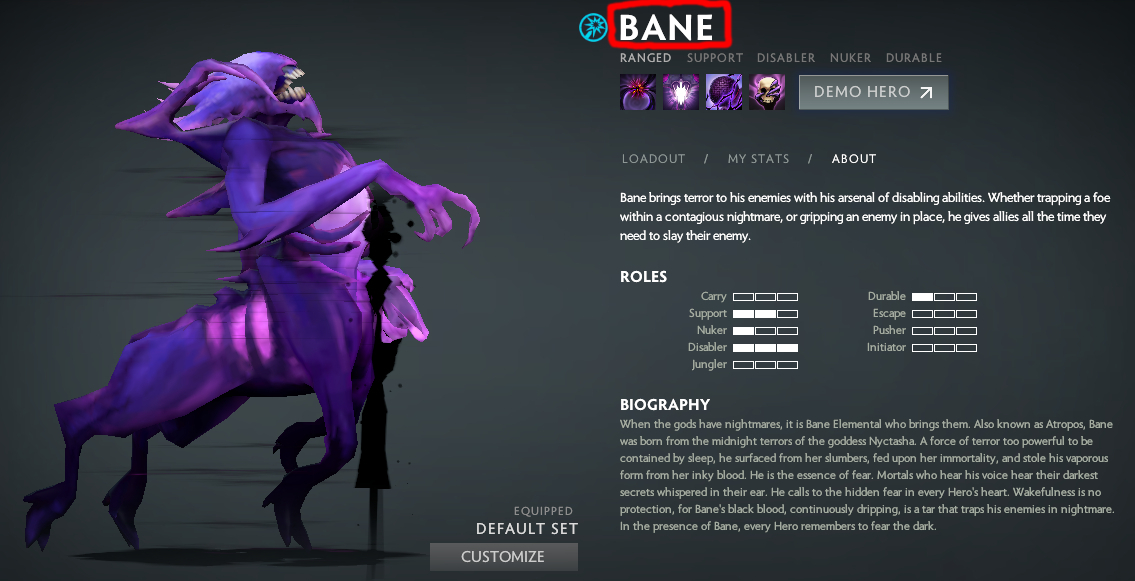
Ada sesuatu yang disembunyikan di gambar lol.jpg dan hint-nya adalah teks di red line, yaitu kata BANE. Extract menggunakan steghide
$ steghide extract -sf lol.jpg -p "BANE"
wrote extracted data to "g3t_th1s.py".
File g3t_th1s.py berhasil didapatkan, dan berisi
#! /usr/bin/python
# Flag = Password
if __name__ == '__main__':
p4ssw0rd = raw_input('passwd --> ')
if len(p4ssw0rd) != 27:
print 'nope'
else:
if ord(p4ssw0rd[25]) != 110 or ord(p4ssw0rd[8]) != 110 or ord(p4ssw0rd[2]) != 116 or ord(p4ssw0rd[3]) != 95 or ord(p4ssw0rd[9]) != 49 or ord(p4ssw0rd[6]) != 101 or ord(p4ssw0rd[7]) != 95 or ord(p4ssw0rd[1]) != 51 or ord(p4ssw0rd[4]) != 116 or ord(p4ssw0rd[10]) != 103 or ord(p4ssw0rd[18]) != 110 or ord(p4ssw0rd[17]) != 95 or ord(p4ssw0rd[12]) != 116 or ord(p4ssw0rd[0]) != 108 or ord(p4ssw0rd[16]) != 51 or ord(p4ssw0rd[22]) != 114 or ord(p4ssw0rd[26]) != 100 or ord(p4ssw0rd[24]) != 101 or ord(p4ssw0rd[23]) != 95 or ord(p4ssw0rd[20]) != 118 or ord(p4ssw0rd[15]) != 114 or ord(p4ssw0rd[19]) != 51 or ord(p4ssw0rd[5]) != 104 or ord(p4ssw0rd[11]) != 104 or ord(p4ssw0rd[14]) != 52 or ord(p4ssw0rd[21]) != 51 or ord(p4ssw0rd[13]) != 109 :
print 'nope'
else:
print 'GGWP m8 ..'
Susun ulang string p4ssw0rd dan dapatkan flag-nya. Operasi pengecekan (!=) diubah menjadi operasi assignment (=) untuk mendapatkan flag-nya
solver.py
p4ssw0rd= [0 for i in range(27)]
p4ssw0rd[25]=110
p4ssw0rd[8]=110
p4ssw0rd[2]=116
p4ssw0rd[3]=95
p4ssw0rd[9]=49
p4ssw0rd[6]=101
p4ssw0rd[7]=95
p4ssw0rd[1]=51
p4ssw0rd[4]=116
p4ssw0rd[10]=103
p4ssw0rd[18]=110
p4ssw0rd[17]=95
p4ssw0rd[12]=116
p4ssw0rd[0]=108
p4ssw0rd[16]=51
p4ssw0rd[22]=114
p4ssw0rd[26]=100
p4ssw0rd[24]=101
p4ssw0rd[23]=95
p4ssw0rd[20]=118
p4ssw0rd[15]=114
p4ssw0rd[19]=51
p4ssw0rd[5]=104
p4ssw0rd[11]=104
p4ssw0rd[14]=52
p4ssw0rd[21]=51
p4ssw0rd[13]=109
flag=''
for i in p4ssw0rd:
flag+=chr(i)
print flag
Flag
l3t_the_n1ghtm4r3_n3v3r_end
Rant
Sebenernya lupa ini soal dari mana, tapi tersimpan di folder bernama Indoxploit maka jadilah ini Soal Indoxploit Stegano 2